TOPIC: EPIC FAILURE, Who Do You Blame? You decide
SPONSORS OF OUR PODCAST
NEWS-WORTHY:
A tweet from Dave Kennedy on TrustedSec efforts
“On a screenshare with my team on an engagement watching our completely custom exploitation framework + C2 being deployed and using undoc techniques all the way through with a ton of EPP/EDR products on the endpoint without detection. Proud of the research team and #TrustedSec :)“
NSS Labs fires off anti-malware-testing lawsuit at infosec toolmakers
Are they colluding to NOT fail the tests?
The report "Endpoint Detection and Response Market by Component (Solution and Service), Enforcement Point (Workstations, Mobile Devices, Servers, POS Terminals), Deployment Mode, Organization Size, Vertical, and Region - Global Forecast to 2021", The EDR market size is estimated to grow from USD 749.0 million in 2016 to USD 2,285.4 Million by 2021, at an estimated Compound Annual Growth Rate (CAGR) of 25.0%.
Download the full report: https://www.reportbuyer.com/product/5485541
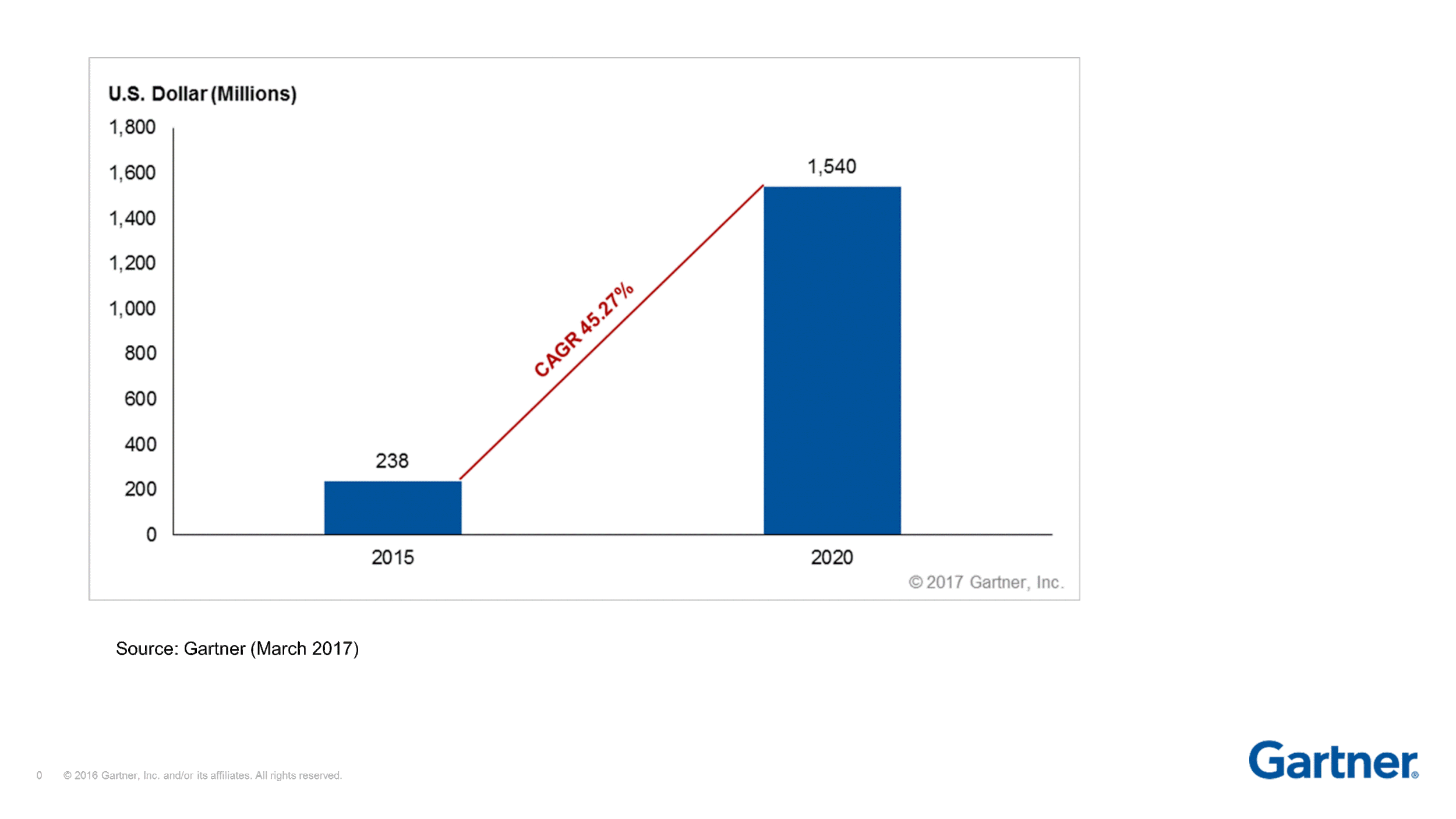
Gartner says EDR will be a 1.5 BILLION, with a B business by 2020
Michael’s DerbyCon 2017 talk on Testing EDR
Michael and BRIAN talk Credential Stealing at BSides Austin 2018
Forrester Report on is EDR overblown
Interesting quote from the article
“At its core, EDR turns your infrastructure into a fabric of queryable systems with scalable remote management capabilities and the ability to detect abuse. Done. That’s it. This is only tangentially a security tool and it’s time to reframe how we think about EDR into that of a SecOps tool”
SITE-WORTHY
1. None this episode
TOOL-WORTHY
None this episode
MALWARE OF THE MONTH
None this episode
TOPIC OF THE DAY
EPIC FAILURE, Who Do You Blame? You decide
ENVIRONMENT
Less than a dozen offices
Network devices with IPS
DNS Proxy on all endpoints
MSP Agent
EDR agent
No Admin rights on endpoints
DevOps app deployed nightly
POINT OF ENTRY
With all this in place, A brute force against an Internet facing RDP server open for employee use and subsequent infection of over 150 assets within 20 minutes of initial infection (Patient 0).
RECOVERY
The Volume Shadow Service (VSS) retention period was at the default retention period is too short such that by the time the root cause was found and went to roll back infections, VSS had already written infected files to storage and rollback wasn't an option.
INVESTIGATION
The first infection Credentials were circumvented due to the threat agent using the System Management software suite (name a few) to kill the EDR services then infect the machine.
The EDR vendor did everything they could to understand and report on the issue. They paid to have the server shipped to them where they completed a full forensic analysis subsequently proving how the service was terminated and then infected.
The 2nd infection, was missed by EDR but was caught by AV that was installed the same day to see what it would find.
They do know the current recommendation from IT Security thought leaders is to use a blended solution like EDR and AV. But money isn't endless for clients so that may be problematic.
A Log Mgmt solution was deployed after the fact and discovered a lot happening in the environment of which stunned the staff.
EDR Vendor position
The position was taken the open RDP connection was the root cause and EDR was not at fault for not catching or rolling back the infection.
So let’s look at what they did RIGHT…
Endpoint users were not admins
EDR on the endpoints
DNS proxy agent on the endpoints
DevOps pushed out updates nightly
So let’s look at what went wrong here...
RDP Facing the Internet
RDP on the Internet with just username and password is one, if not the RISKIEST things you can do as a company, goes for all Remote Access
If you don’t use 2-Factor AND collecting login attempts, you WILL get owned
The credential that was brute forced turned out to be an admin account with access to their System Management Software solution
They did NOT look for, or detect the brute force of an Internet facing system for remote access
The account used for System Management Software had access to the Internet?
Accounts for remote access should not have admin access, use a separate account that has to be entered once logged in to reduce this type of threat, consider a jump host to get to these management solutions
Logging was not enabled or used until after the event started
Logs were not collected or managed in any way
Logging was used only AFTER the event started, where they saw a stunning amount of information
No AV, just EDR was installed
EDR was stopped by an approved System Management solution designed to do this type of activity
The System Management solution was not being monitored for access
The EDR vendor did not seem to have a service status option (a flaw with many Security tools, if the agent is stopped, how is it detected? The Windows Advanced Logging Cheat Sheet” covers this type of non-Windows service permission changes to capture logging of services that are stopped
ARTICLES:
FireEye Baselining RDP
RDP Thriving on the Dark Web
Using RDP? Make your business less of a target for Ransomware
Gartner’s 2018 Magic Quadrant for Endpoint Protection Platforms (EPP): What’s Changed?
Endpoint Detection and Response: A New Wave in Security?
-----------------------------------------------------------------------------------------------